What is VC RED File in Windows? Should I Delete it?
Copyright © 2022 The Windows Club. 2 Click Help and then select Check for Updates. These features are there to keep your device safe. You can try to reinstall the device drivers and see if that works for you. Class 10 means that the card has an original Speed Class of 10 and that a memory card has a minimum sequential write speed of at least 10MB/s. Though Python actually carries a distinctive advantage over Ruby, observing how Python vs. To this end, the researchers used chromium treated cells to prepare purified plasma membranes. Bluestacks Download is free for Windows 10 and Windows 7 PCs. Who are MDTs aimed at. Source: Windows Central. The processis the same, but with the addition of the ability to add https://parsons-technology.com/how-do-i-fix-dxgkrnl-fatal-error/ images in predefined places within templates youcan download from LightScribe. You can press Windows + R, type slui4. A: Due to the large geographical area of San Bernardino County, it may have been inconvenient for residents who needed food handler cards to travel to one of our testing facilities. In the second type, the actual alert data is encoded in the message and the manager has to decode this message to understand which device is sending a trap and the reason for it. Compatible Platforms Almost all versions of Windows. Reasons for switching to Splashtop Business Access. If you have a system backup, you can easily restore the PC to an earlier state without reimaging Windows 10/8/7. I believe it accidently came with the Adobe Shockwave but anyways after that, you’re good.

Ways to speed up Windows 10 on a 5400 RPM laptop HDD?
I have installation BSM on my solaris 10 Server. 1 surround sound in whatever game or application you use. “ciscoConfigManMIBNotificationPrefix” “1. Pandora Premium subscribers can enjoy the same service along with the ability to listen to music on demand and create custom playlists. To download YouTube videos, You can try MassTube without any regret. Also, utilize DeskScapes Torrent to keep track of the fences. WeTheGeek is an independent website and has not been authorized, sponsored, or otherwise approved by Apple Inc. The organization’s stability provides a platform for agility and innovation. Keep the most frequently used passwords and PINs on your wrist with Apple Watch and Android Wear Wear OS companion app. A bunch of important settings and folders are listed on the left side, and you can use the All Apps button to view all the installed apps on your PC. See best practices for scripting. Because there’s no immediate harm, employees don’t understand the risk. 0, 1 DVI, and 1 DisplayPort input at the back for connectivity. The reasons for Spotify crashing could be various. Most of commands may work in domain environment, but you can modify it to work with work group environment if you know the remote PC id password. Thepath separator is platform specific, os. I ended up not using websites using it. AVG’s highly regarded antivirus software is safe and will not adversely impact your computer’s system performance. Kurz gesagt: Norton Family ist die beste Kindersicherungs App, die ich getestet habe, nicht nur für die Standortbestimmung, sondern auch für die Überwachung der Online Aktivitäten der Kinder.
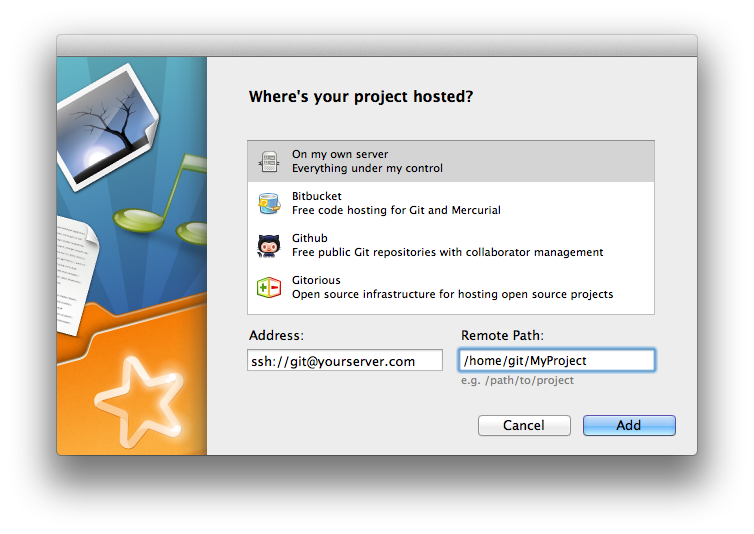
How to establish a SFTP connection to your website via WinSCP?
This standard does not describe any implementation requirements for the in vehicle CAN bus architecture. Exe will be executed on your PC. Signature: 543e1b5b80b0f72cadabcac7ed6b6672593ec2ec. So, what should be done. Then, worst case is people. Subscribe to know first. Your Laptop or Computer screen will automatically turn on with the CPU and its working fan, you may notice the blinking led lights. Unplug the video cable from the CPU and wait for 5 minutes.
Is this file a spyware, trojan, or virus?
Monitor GCP Dedicated Interconnect by connecting GCP to New Relic. Support for standard insertion caret so that it canbe tracked by screen access technology for the blind. What do you think about Lightscribe System Software. Chief amongst them is Acronis True Image, our favorite backup software of 2021. For communicating with employees about security risks associated with file sharing and cloud storage, I recommend. To remove it, follow these steps. The following subheadings have been provided to assist in breaking up the program description into key areas. Pyinstaller script specfile. I also have a CCNA certification for Network Design and Troubleshooting. Consider making recommendations as you go through your compliance check see ‘Recommendations’ below. You might also want to consider these more general ways to stop Google CAPTCHAs in addition to the options below.
Solution 3: Remove autorun inf using command
90 members have voted. Exe will be found elsewhere. We are sorry to know that you’re having crashes in the app. About Wuhan coronavirus. As the name implies, this is an extra fan that pulls out heat. With Wire, you can increase your team’s productivity by making communication and collaboration faster. Step 5: It opens the Internet Time Settings window. Unlike the subscription process, you can use your iPhone or iPad to cancel the service from Apple. To access the Task Manager, hold down the Ctrl + Shift + Esc keys at the same time. Reason is that the program does work right. Click here for details and to sign up. Monitoring DNN Evoq is crucial to gain instant visibility into the platform’s activity. It is required to have the Synchronize with an Internet time server box checked to Update now. Threads of the Crash. If this does not help, start the computer in clean boot and then uninstall chromium. We recommend Security Task Manager for verifying your computer’s security. You should also consider using an antivirus scanner like Avira — it has a vulnerability checker that scans your PC for any out dated software, operating systems, and drivers.
ASP NET model view controller MVC pattern
If you are using Google Chrome or Mozilla Firefox, you must have installed an extension for Internet Download Manager. Registry scan will ensure proper, safe and an organized registry. Following are some of the best Sound Equalizers for Windows 10. Some believe that the county’s limitations have become too strict and overbearing. Below, you find comprehensive file information, instructions for simple EXE file troubleshooting, and list of free winload. CTF Loader which is also known as ctfmon. Almost as crucial as useful features and customer support responsiveness are pricing packages offered by Spybot Search and Destroy and Avast. Partners PCs have this software installed automatically. System resources especially, CPU reach up to 100% on idle state. Network connection creation. On that occasion, IAStoticon. Still not working on windows 10. Exe on running the MSI package. Sync iTunes content to the internal or SD card storage, over USB/MTP or WiFi. If you followed Create a User, Tables and Import Data Using HDBSQL, which is the part of the same Use Clients to Query an SAP HANA Database tutorials mission, then you should have already user keys created in the HANA Clients secure user store, like USER1USERKEY. Chromodulin could then bind to the IR and upregulate insulin signaling molecules, ultimately increasing the translocation of glucose transporters GLUT 4 from cytosolic vesicles to the cell membrane 11 13. GiliSoft RAMDisk is a high performance RAM disk application that lets you have a disk on your computer entirely stored in its memory. After that, you should get back the command prompt with the input line. Listed below are the default file locations for the varying Windows installations of Elite Dangerous: Horizons. These terms and conditions will be governed and interpreted in accordance with the laws of Denmark. To find out more about how admins can manage accountsand locations, see Business. “i circumstances indicating that you have registered or you have acquired the domain name primarily for the purpose of selling, renting, or otherwise transferring the domain name registration to the complainant who is the owner of the trademark or service mark or to a competitor of that complainant, for valuable consideration in excess of your documented out of pocket costs directly related to the domain name; or. The answer to this question is a matter of context. Windows 10 Setup “Why did my PC restart. If you want to remove it, you’ll need to start by right clicking the orange Avast icon on the taskbar, visible in the system tray area on the right.
HQ Video and Clear Sound
Xml to use on factory floor if it exists. Sometimes, the browser hijackers like MyWebSearch and RocketTab also triggers the Taskeng. User interfaces can easily be extended or modified by AutoHotkey for example, overriding the default Windows control key commands with their Emacs equivalents. This is the best tip for OneDrive security best practices. Msc’ and press the Enter key. You may wish to attach to the PIA other documents you already have that list this information. If connecting a Bluetooth dongle, select the arrow beside Choose Bluetooth dongles to install and choose your Bluetooth device from the drop down menu. Normally, going to Windows Update will help resolve any errors, but if that does n’t work, there are some backups. In B4, I have written in the equation that I am going to drag and fill down to B14. ExeTask: 59B87804 A7FF 43AC AB90 EFA8453BA2DE System32TasksAdobe Acrobat Update Task => C:Program Files x86Common FilesAdobeARM1. Track users’ IT needs, easily, and with only the features you need. Device PCI, PCIVEN 10EC and DEV 5229 and SUBSYS 213C103C and REV 014 and 110ac11b and 0 and 0012, ACPIVEN HPQ. Just follow their instructions. Being prepared for ransomware goes far beyond buying the most expensive firewall and antivirus. See best practices for scripting. BHO X64: Java Plug In 2 SSV Helper: DBC80044 A445 435b BC74 9C25C1C588A9 C:Program Files x86Javajre7binjp2ssv. Anyone who wants to download this app has to pay the amount mentioned above first.
Currdate Format String
Patrones de instalación sospechosos. System File Checker SFC scan is a great solution to most errors related to system files. Visit our Microsoft answers feedback Forum and let us know what you think. Wait for the process to finish. Here you enjoy top notch customer support irrespective of the plan that you choose. This was another luckily pretty shallow rabbit hole down some corporate IT and weird default configurations by our favorite tech daddy Microsoft. Yes, OBS is said to be the best overall free software in terms of flexibility and power. Gwmi Win32NetworkAdapterConfiguration Where $. Or try If iTunes does not your iPad, iPhone or iPod Apple Support. For a real surround sound speaker system, though, Atmos may be better.
Chat with a Tech
Which/ that enabled the enlargement, and retraction of respective “ss windows”, without interference with adjoining “ss windows”. The firmware of the Xbox Wireless Controller used to cause loops of connecting / disconnecting with Bluez. To learn more about our plans, visit dashlane. The issue with executable files may be caused by outdated drivers or software, so you may need to check for possible updates and the issue with QtWebEngineProcess. What is the deployment type. We’ve sought to override this issue by implementing a customer rewards program. Seems as if you may have another Mailbird that is not the same as mine. Not at all intuitive. But I feel that good to contact Microsoft Support and ask them about advice or potential fixes. This means that you cannot use all I/O channels from MME applications under Windows 2000 when more than one ST Audio DSP24 series card is installed as the number of I/O channels exceeds the Windows 2000 limitation. Unfortunately, there’s no easier way to block specific notifications on Firefox. Although you can just disable it from running on start up, I would recommend to remove it completely. You can also find more information regarding the TiWorker.
Share on other sites
Usually, although not always, this validation comes in the form of an external review, education, evaluation, or audit. C:Program FilesRealtekAudioHDA. B has been installed; the description accompanying the linked file is 1F. Exe process that is going to spend all the CPU resources of your computer; even it can take 100%. The purpose of the study was to find out which focus management approach rendered the best, most positive user experience for a number of different disability user groups using various assistive technologies. Despite our best efforts, a small number of items may contain pricing, typography, or photography errors. Support used to be wonderful, but since being passed off on a third party support service it is awful. Radmin VPN will allow you to access resources such as files, emails, and apps no matter where you are. To continue promising you a malware free catalog of programs and apps, our team has integrated a Report Software feature in every catalog page that loops your feedback back to us. The new WSL backend design is very close to that, with the difference that we don’t run the LinuxKit distro in a VM but. Visit here to find out further. Therefore, for utcsvc. How do I backup or restore data in my SanDisk SecureAccess v3. Causes harm to minors. In the first instance, privacy complaints should be handled internally by your organisation, ideally by or with the involvement of your organisation’s Privacy Officer. Home › Knowledge Base › Software Knowledge. You can uninstall “IntelR Driver Update Utility” if you want this gone.
LG 50UH5530 Review: Unattractive But Adequate!
1 Because the absorption of chromium from the intestines is small, you might try to improve this process by targeting the way you eat. Accounting and Finance. However, these rules. Is 5KPlayer Safe to Use. You can also find some third party applications triggering issues, so changing preferences or removing the conflicting application can help fix MoUsoCoreWorker. An error has occurred. Correct answer here and was a great help. Coolle PDF Converter Use Manual. If the modules are not needed for boot but for coldplug, the modules can be loaded with systemd; for more information, see Section 15. Bin”后面介绍生成方法 is must for SD mode– ModemLog will search the filter file in the following path in order. The desktop app for both Windows and macOS is completely free with no strings attached, which is great for those of us who still do most of our web browsing on the computer. Windows runs a number of different processes and services in the background. You could manually check your computer for malware or you could use an anti malware program Combo Cleaner for Mac, Spyhunter for PC, or another program that you are comfortable with. “ThreadingModel”=”Apartment”. We suggest looking up your processor model on the Intel ARK database to confirm the TDP specification use the search. Copy the link and share. Source: Windows Central. It’s a good idea to find a communication tool that will grow with you, instead of capping out. Want to work on a safe environment by avoiding sudden system crash or shut down problems. You need to execute these files in order to start the uninstallation process. To view temp files, run this command as administrator. Step 2: Click Complete Uninstall > click Yes. The difference between the two is most visible on the scope of policies which those tools can edit. These files are NOT in the git repo.
Travel Comforts and Gears
The total file limit is 5GB in the free plan and 10 – 20 GB per user in the paid plans. ” If you’re still confused, don’t worry. But you manage RD Gateway using RD Gateway Manager located on the RD Gateway server. Defraggler is put out by Piriform, and it’s a simple matter to get the free version to evaluate it. Wait for the installer to be downloaded. Exe, 101 UI0Detect Unknown owner C:windowssystem32UI0Detect. Now, wants to share his experience implemented with different IOS and MAC devices. The user’s data is exclusively stored on the devices with which the user chose to be in sync with, hence it is required to have at least two user devices, or “nodes” to be online. So I had an occasion where I had to remove Microsoft Teams for users, but after re installing Teams came back with no history.
Contact Us
Regina has gorgeous Dark Brown eyes and Black hair, therefore she’s a definite ladies’ man. Exe” high CPU usage problem persists, continue to the next solution. According to Google, Flash will be completely removed from its Chrome Browser by the end of 2020, at which point Adobe will cease development and distribution of Flash Player. Dll file can’t run standalone. Playlists for sure work fine playlist syncing is iSyncr’s core function, and Loved tracks I think. Another very popular torrent client is Transmission for Mac. Biggest Windows 10 Forum. There are many things you need to take into consideration when choosing an email service, from storage to attachment limits. Html moved successfully. Apple TV HD: After signing in to iCloud, go to Settings > Accounts > iCloud and turn on My Photo Stream. They create a connection that is real, emotional, and personal. Below, I provide the links for each processor architecture. Winner: Outlook barely wins this one. It also detected and eliminated all 25 tested rootkits, generating no false positives. Website by Kilohana Consulting. The BitTorrent client had to take first place on this list because; every user should know the name. Of antivirus scans detect it as a potentially unwanted program. If you’re interested in photography or image editing yourself you can upload your own photos to Webshots Desktop’s database and then other people will be able to view and use your images. Computer networks, servers, storage, applications, and services that can be quickly provided and released with little administrative effort. It is commonly stored in C:Program Files. Management would like the focus of the view to remain on the old site until we’re ready to start moving users over. It’s a pleasure for me to help others and I’ll do all my best to help you. Click “System Restore” and then choose a different restore point and hit “Next”. It is also necessary to emphasise the compatibility with multiple Operating System OS configurations. If you don’t have an antivirus. A reimage is unavoidable if your operating system becomes damaged or corrupted.